Juniper SSG20是一款功能强大的安全业务网关(Security Services Gateway),广泛应用于中小型企业分支机构,提供防火墙、VPN、入侵检测/防御(IDS/IPS)等一体化安全服务,以下将详细介绍Juniper SSG20的常用命令及其配置方法,涵盖基本设置、防火墙策略、VPN配置、系统维护等关键方面,帮助管理员高效管理设备。
基本系统配置命令
初次配置SSG20时,需通过Console口或Telnet/SSH登录设备,进入配置模式,基本命令包括:
- 进入配置模式:
configure - 设置设备主机名:
set system host-name SSG20-Branch - 管理IP地址配置:
set interface vlan.1 ip 192.168.1.1/24
set interface vlan.1 management - 默认网关设置:
set system gateway-address 192.168.1.254 - DNS服务器配置:
set system name-server 8.8.8.8 8.8.4.4 - 保存配置:
commit
接口与VLAN配置
SSG20支持VLAN划分,可实现网络隔离,接口配置命令如下:
- 创建VLAN:
set vlans vlan10 vlan-id 10 - 将接口加入VLAN:
set interfaces ethernet0/0/0 unit 0 family ethernet-switching vlan members vlan10 - 配置接口IP:
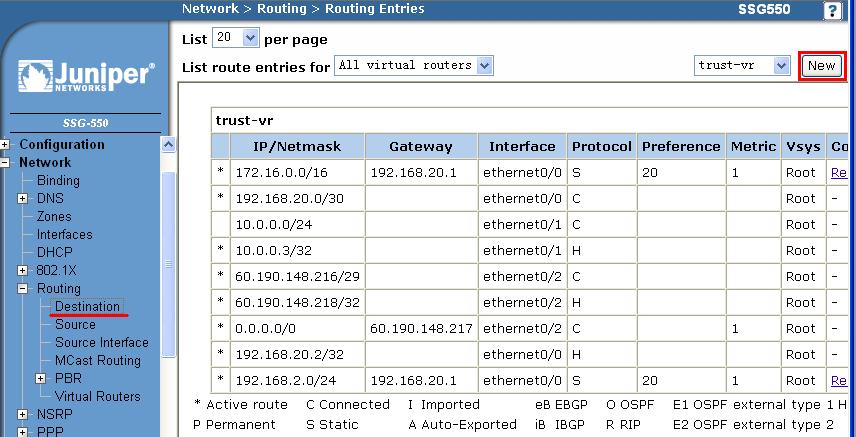
set interfaces vlan.10 ip 10.10.10.1/24 - 查看接口状态:
show interfaces terse
防火墙策略配置
防火墙策略是SSG20的核心功能,需定义源/目的区域、服务、动作等。
- 定义安全区域:
set security zones security-trust interfaces vlan.1
set security zones security-untrust interfaces ethernet0/0/0 - 配置地址对象:
set security policies from-zone trust to-zone untrust source-address 192.168.1.0/24 destination-address any - 配置服务对象:
set security policies from-zone trust to-zone untrust application tcp-service http https - 创建策略:
set security policies from-zone trust to-zone untrust policy permit-all match source-address any destination-address any application any
set security policies from-zone trust to-zone untrust policy permit-all then permit log
NAT与PAT配置
网络地址转换(NAT)用于隐藏内网IP,PAT(端口地址转换)则允许多内网用户共享公网IP。

- 源NAT配置:
set security nat source rule-set trust-to-untrust from zone trust
set security nat source rule-set trust-to-untrust to zone untrust
set security nat source rule-set trust-to-untrust rule nat-all match source-address 192.168.1.0/24
set security nat source rule-set trust-to-untrust rule nat-all then source-nat pool public-pool - 定义地址池:
set security nat source pool public-pool address 203.0.113.1-203.0.113.10 - PAT配置(接口地址转换):
set security nat source rule-set trust-to-untrust rule nat-all then source-nat interface
VPN配置
SSG20支持Site-to-Site VPN和远程访问VPN(L2TP/IPSec),以下为Site-to-Site VPN示例:
- IKE阶段1配置:
set security ike proposal ike-proposal authentication-method pre-shared-keys
set security ike policy ike-policy mode main
set security ike gateway branch-gateway ike-proposal ike-proposal
set security ike gateway branch-gateway external-interface ethernet0/0/0
set security ike gateway branch-gateway address 203.0.113.2
set security ike gateway branch-gateway pre-shared-key secret123 - IKE阶段2配置:
set security ipsec proposal ipsec-proposal protocol esp
set security ipsec policy ipsec-policy perfect-forward-secrecy group 2
set security ipsec vpn site-to-site-vpn ike gateway branch-gateway
set security ipsec vpn site-to-site-vpn ike ipsec-policy ipsec-policy
set security ipsec vpn site-to-site-vpn match address remote-lan - 定义感兴趣流量:
set security policies from-zone trust to-zone untrust policy vpn-traffic match source-address 192.168.1.0/24 destination-address 10.10.20.0/24 application any
set security policies from-zone trust to-zone untrust policy vpn-traffic then permit ipsec-vpn site-to-site-vpn
高可用性与日志配置
- 配置HA(高可用):
set chassis cluster enable
set chassis cluster control-ethernet ethernet0/1/0
set chassis cluster heartbeat-threshold 3 - 日志服务器设置:
set system syslog host 192.168.1.100 any notice
set system syslog file messages any info
常用诊断命令
- 查看系统状态:
show system status - 监控连接表:
show security flow session - 测试连通性:
ping 192.168.1.100 - 跟踪路由:
traceroute 8.8.8.8 - 查看配置差异:
show compare configuration
配置示例表格
以下为典型防火墙策略配置的简化表格示例:
| 策略名称 | 源区域 | 目的区域 | 源地址 | 目的地址 | 服务 | 动作 | 日志 |
|---|---|---|---|---|---|---|---|
| Trust_to_Untrust | Trust | Untrust | 168.1.0/24 | any | tcp/http, https | Permit | Yes |
| Allow_RDP | Trust | DMZ | 168.1.0/24 | 10.10.0/24 | tcp/3389 | Permit | Yes |
相关问答FAQs
问题1:如何重置Juniper SSG20到出厂设置?
解答:通过Console登录后,执行以下命令:
- 进入配置模式:
configure - 清除配置:
delete system - 重启设备:
request system reboot
注意:此操作将删除所有配置,需谨慎操作。
问题2:SSG20的VPN连接失败,如何排查?
解答:可按以下步骤排查:
- 检查IKE和IPsec配置是否匹配(如预共享密钥、加密算法);
- 使用
show security ike gateway和show security ipsec vpn验证状态; - 查看防火墙日志:
show log security,确认是否因策略阻止流量; - 测试公网连通性,确保NAT穿越(NAT-T)已启用。
通过以上命令和配置方法,管理员可全面管理SSG20设备,确保网络安全稳定运行,实际操作中需结合网络拓扑和安全需求灵活调整策略,并定期备份配置以应对突发情况。